Over the last couple of weeks, I’ve seen a lot of information about various products from Microsoft.
Azure
A distributed operating system for the “cloud”. The idea here is that you write to the Azure API on your desktop. Run / debug it on the desktop. When you deploy it to Azure, Microsoft will run this on “server” fabric. You don’t have to worry about individual servers, scalability etc. Since your code could end up running on different servers due to load balancing, all state information must be stored centrally. Azure provides a distributed storage and a distributed SQL Server data storage to address these requirements. Azure is in CTP. You can download the SDK and play around on your own PC. If you want to deploy to Azure, you’ll need a invitation token (these were given out in PDC 2008). For the development machine, you need Windows 2008 or Vista, Visual Studio 2008.
MDM BullDog
Microsoft acquired Stratature’s MDM product (eDM). This is a robust MDM tool that is in its 4th generation. Profisee is the firm spun off by ex-Stratature employees. Ian from Profisee gave an excellent introduction to this tool. What I liked was its out of box Web UI, Workflow, Business Rules and a solid BI focus.
Geneva
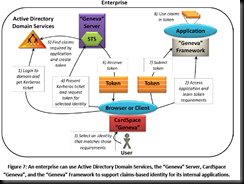
This gets exciting. In the Identity space, there is a shift from applications managing your identity (uid/pwd) to claim based authentication/authorization. To use an application (RP-relying party), you need to provide a token with the appropriate claims from a trusted STS. The IP (Identity provider) STS (Secure Token Service) issues you a token with the claims, after you logon to the STS. It signs the token with a private key. The RP can decode the token and extract the claims to decide whether the user is allowed to use the application. So why is it exciting?
The IP can be Yahoo OpenID, Google, Microsoft Live or even a self issued IP. Your app can choose to trust all these STS’s; or a better way is to trust a single STS and ask the user to get a token from this STS using the token from the first STS. This provides a transparent way to federate identity. Everything is service based that makes it easy for active / passive logon. Geneva provides 3 components – Geneva server which is a Windows based STS, Geneva Cardspace which is an identity selector and Geneva framework which is an API for applications that need to use Geneva. The nice thing is that these are not bound and are based on open standards (WS-Trust, SAML, WS-Security). While searching for this, found that WCF provides a wsFederation binding that can handle claim based authentication in WCF.
Cardspace Identity selector
Enterprise case
Internet case
Using external STS
Multiple STS





No comments:
Post a Comment