Thursday, October 22, 2009
SharePoint Resources
See study on Kraft sites and Kroger sites.
Monday, October 19, 2009
Insulating an Unfinished Attic Tutorial
Keeping this link for future home projects. It takes you step by step through the process of insulating your attic.
Friday, October 16, 2009
Extending Sharepoint search with custom properties
Situation:
Empower.Me would like to store marketing documents, pictures, PDFs etc in Connect Share. The items are stored in a Sharepoint document library with a custom content type. This custom content type has additional properties that further describe each item. These properties are business relevant and help in categorization. Examples: Validity dates, Philips business unit, CTN or product identifier, etc.
Some of these properties can be mapped to standard (out of box) Sharepoint properties, but some are new to Sharepoint.
EmpowerMe would like to find the documents that match certain property values (instead of a full text search).
Investigation results:
The Connect Sharepoint environment built on Microsoft Office Sharepoint provides 3 standard methods for searching items.
- Search page (https://www.emea.sharepoint.philips.com/Search/Pages/results.aspx)
- Advanced search page (https://www.emea.sharepoint.philips.com/Search/Pages/Advanced.aspx )
- Search web service (https://www.emea.sharepoint.philips.com/sites/TS0903310710272080427802/_vti_bin/search.asmx?WSDL)
The results returned by these three alternatives are identical.
All of the above methods permit you to search by keywords / property values or by full text. To query a property, just include <propertyname>:<value> in the query. If the value has a space, enclose it within double quotation marks. An example of this is in Exhibit 1.
Exhibit 1: Search for PDF documents by author (Rinia, Jornie) in the empowerMe site
Site:https://www.emea.sharepoint.philips.com/sites/TS0903310710272080427802/ filetype:pdf Author:"Rinia, Jornie"
Now let us try this syntax on items with custom properties. We take an item from the EmpowerMe Document Library. This item has a custom property “ChapterName” = “Introduction to empower.Me”. It also has a standard property “Title”=”Introducing the empower.me…..”. (See Exhibit 2)
Exhibit 2: Item with a custom property “ChapterName”
A search on documents with content type “Empower.me Guideline” shows up 3 documents.
Exhibit 3: Search for ContentType “Empower.me Guideline”
Site:https://www.emea.sharepoint.philips.com/sites/TS0903310710272080427802/ Author:"Vaassen, Guido" ContentType:"Empower.me Guideline"
A search on the property ChapterName doesn’t seem to work. It returns no results. (see Exhibit 4).
Exhibit 4: Search for ChapterName containing Introduction
Site:https://www.emea.sharepoint.philips.com/sites/TS0903310710272080427802/ Author:"Vaassen, Guido" ChapterName:Introducing
However, if you search on Title, you get these two results. See Exhibit 5.
Exhibit 5: Search for Title containing Introducing
Site:https://www.emea.sharepoint.philips.com/sites/TS0903310710272080427802/ Author:"Vaassen, Guido" Title:Introducing
So it appears that custom properties are ignored by the Search in Connect Share.
However, looking a bit deeper, you can see that there is a standard way to extend Search to consider these custom attributes. A bit of background first.
When the search engine “crawler” indexes items in Sharepoint, it stores all custom properties in the index as “Crawled properties”. These crawled properties are ignored during search (except if it is a string, it will be included in the full text search for that item). The custom property “ChapterName” is included in the crawled properties. Microsoft Office Document properties are also available as crawled properties.
The properties that are available for searching are called “Managed properties”. You must create a new Managed Property and map it to your “crawled property”.
Fortunately, extending search for your own attributes does not require any programming or coding. Instead, creating and mapping a new managed property can be done in a few minutes by a Sharepoint site administrator. (See instructions at http://j.mp/3BnZnQ and http://j.mp/3ulrlT )
Once you have a managed property, the administrator can change the search options for this managed property.
· In the Search Options section, select Include this property in Advanced Search options to allow users to perform advanced searches using this property.
· Select Include this property in the content index to include this property in the content index, so you can search for items based on this property.
· Select Allow property to be displayed to make this property available for display in custom search applications.
· Select Display this property in item details in search results to display this property in the Item details section for each item in search results.
An additional enhancement is the concept of search scope. Search scope restricts the selection of documents that are returned. As an example, a search scope called Marketing can be setup to search all items with the content types setup for marketing, like “EmpowerMe guidelines”.
Conclusion
Connect Share can be quickly extended to add additional properties that are relevant to a parametric search. Parametric search combined with scope provides a method to make search more relevant to the users.
External web references:
Searching on property values in Microsoft Search: http://j.mp/WGAjh
Program to list all crawled and managed properties in Sharepoint (Need sharepoint administrator access to /ssp/admin):
Generate a Extending Microsoft search for image search: http://j.mp/1Gqj93
Managing “Managed properties”: http://j.mp/3BnZnQ and http://j.mp/3ulrlT
Monday, October 12, 2009
Virus, Spyware & Malware Protection | Microsoft Security Essentials
You don't need to buy an antivirus package anymore!
- Posted using BlogPress from my iPhone
Monday, September 28, 2009
Posting on the fly

Thursday, May 21, 2009
P2P networking
To start with Peer to Peer networking, install the Peer 2 Peer component (XP – Add remove programs>Add remove Windows Components>Network components>Peer 2 Peer).
Turn on your IPv6 stack.
net start p2psvc
netsh p2p pnrp cloud show list
I was not able to connect with the seed server
netsh p2p pnrp diag ping seed
To turn on Teredo based IPv6 for your PC. On XP – make it the DMZ server if behind a NAT firewall or redirect ports 3544 and 3540 to your machine.
netsh interface ipv6 set teredo client teredo.ipv6.microsoft.com
netsh interface ipv6 set teredo enterpriseclient(if on a Domain)
(I also found teredo.alicenet.de but it did not give me an address).
The IGD tool from Microsoft helps you evaluate your network connection to the Internet.
A nice diagram on connecting IPv6 and IPv4.
A good post on setup of IPv6 (with Teredo) at home; setup of IPv6 with tunnelbroker and more at this link.
This post discusses how you can setup a Teredo broker (Miredo). It also lists some Teredo servers around the world.
When Teredo is running on my PC, I am able to ping6 ipv6.l.google.com; but I cannot get IE or Firefox to use IPV6. Both browsers use IPv6 when I use the Hexago Gateway IPv6 Tunnel client.
Installing Ubuntu 8.1 (Incredible Ibex)
Download the ISO from the Ubuntu site. It was very easy to install, however the updates took quite a while (2 hrs @ 16Mibps).
Links
Setup FreeNX for a fast remote desktop client
When looking at the out-of-box applications, I got interested in the VOIP softphone (Ekiga).It has a Windows client as well, but that was not easy to locate. I got a free SIP address for myself. (sip:cs905s@ekiga.net)
While going through the setup of Ekiga, the NAT detection gave “STUN test result: Port restricted NAT”. Since I didn’t get any meaningful explanation on Google, I opted to enable STUN support. For a headphone, I opted to pull out my Bluetooth USB adapter and hook it up to the Motorola Bluetooth headset. (Lost the manual and found this nice tutorial on the net. I must wait for 2 hours for the headset to charge. I need to figure out how to connect the headset to the USB. Not that simple?Rather easy compared to Windows XP)
Ekiga provides a call out service (diamondcard.us) where I created a divyamahajan account. However it is still on a security hold even after the paypal payment was done.
Eventually, Ekiga did not work.
Decided to throw in the towel and leave it.
IPv6 native providers ISPs
rh-tec.de does provide native IPv6 in Germany. They are on the pricey side however.
For a longer list of native IPv6 providers, try this link at Hurricane Electric. Their state of IPv6 report is worth reading.
Tuesday, January 13, 2009
Linking popup information with Apture
www.apture.com provides a simple way to embed information from other sites into your webpage. It is useful to link multimedia files, Wikipedia lookups etc., without requiring the user to leave the context of your web page.
Thursday, January 08, 2009
Cleaning up your Start menu
Most of the times when you install a new application, shortcuts (*.lnk files) are created as well to help you to launch the application faster. Desktop, start menu and user’s document are the common location where you can find the shortcuts. The shortcuts are useful as long as the applications are not uninstalled from your system. Once the shortcuts are broken, it could become a problem to your Windows.
Most of the cases, shortcuts become broken when you remove or uninstall programs that have shortcuts using the Add/Remove Program in the Control Panel. The un-installation is never clean, leaving leftovers behind e.g. broken shortcuts. These shortcuts are no longer needed; therefore need to be removed from your Windows.
To find all the broken and invalid shortcuts on your system can be a tedious and time-wasting job to you. Instead of doing it manually, you should try Orphans Remover. Orphans Remover is a freeware Windows application that searches and deletes broken shortcuts (*.lnk files) on your Windows desktop, start menu, recent documents and more. On the main window of Orphans Remover, you can specify the folders that you want to scan for broken shortcuts. Orphans Remover can search for broken shortcuts in Windows start menu, desktop, favorites, history, recent documents, temp directory, program files and application data. You also can expand broken shortcuts scanning to include files on removable drivers, a network, CD-ROM drives and RAM disks. Besides, Orphans Remover supports for user defined folder where you can scan others directories for broken shortcuts other than the available locations.
After specifying the locations for scanning, click the “Start Scan” button to scan for broken shortcuts. After a successful scanning process, all the broken shortcuts are displayed. To delete the broken shortcuts, click on the “Delete Orphans” button.
Monday, January 05, 2009
Creating a IPv6 subnet at home
With multiple computers at home, I want to setup all with IPv6 addresses. For that need to get some questions answered:
1. Who will assign me a set of global unicast IPv6 addresses that I can use?
2. How will IPv6 traffic get routed between these computers to other IPv6 computers?
Since my ISP (Hansanet Alice) does appear to support native IPv6, I must use a IPv6 tunnel over IPv4. I will use the Freenet6 (Go6.Net) service with Hexago Gateway6 client.
After a lot of reading, the actual setup turned out to be surprisingly easy.
Setup
Windows XP (Gateway6 client and router) – Install the Gateway client. First verify it is working and then set it in router mode. Here are the steps I used - In the Gateway6 client application, click the Advanced tab. At the bottom, select the “Enable Routing Advertisements”. Select the LAN or wireless interface that is your local network. (IMPORTANT: If you don’t select a valid interface, netsh crashes when you try to connect).
Windows Vista (automatic IPv6 configuration) – Ensure the Vista machine is connected to that network. Restart the machine or simply disable and re-enable the network adapter. (Start Run “ncpa.cpl” and disable / enable the LAN or wireless connection).
Windows XP (automatic IPv6 configuration) – Check if IPv6 is installed (From the command line, ipconfig /all. IPv6 is installed if there are any fe80:* addresses. Install it with “ipv6 install”.) Restart the machine or simply disable and re-enable the network adapter. (Start Run “ncpa.cpl” and disable / enable the LAN or wireless connection).
In both cases, you can use “ping –6 ipv6.l.google.com” to verify that you are connected to the IPv6 internet.
The real test is to check if your machines can be reached from outside by other IPv6 machines.
Useful commands
ipv6 if 1 -- See ipv6 details of the interface. Change the number 1 to other numbers to see other interfaces.
netsh interface ipv6 show address – See all ipv6 addresses assigned on your machine.
netsh interface ipv6 show route – See route on your machine.
VMware virtual machines
The above setup worked with VMware virtual machines with two caveats. The network adapter should be in “bridged” mode and it should be connected to an ethernet interface (VMware does not support IPv6 when you bridge to a wireless card -- forum bug report post).
Nice links
Microsoft’s introduction to TCP/IP
Friday, January 02, 2009
Getting on to the IPv6 bandwagon
While waiting idly for a download to complete, I decided to see what would it require to move to IPv6 on my home network. A quick search indicated that my ancient Netgear WG834GB does not support IPv6. I got a bit distracted by Jonathan’s pages on installing OpenWRT on WG834G. The WG834GB runs a Linux variant and you can telnet into the machine and look around. However I don’t have an alternate wireless router so I did not take the risk of installing OpenWRT.
After reading more about IPv6, I decided to go ahead and take a plunge. Hexago had a nice article on how to go about with IPv6 over IPv4. Microsoft gives a good overview on home setup of IPv6.
I went to go6.net and got registered as cs905s. Downloaded and installed Hexago’s Gateway6 client from go6.net. Start up the client and enter the broker address (broker.freenet6.net) and your user/password. It connected and provided me an IPv6 address (2001:05c0:1000:000b:0000:0000:0000:1b5d) and a brokered address
Later I used another broker - broker.aarnet.net.au. I created another cs905s account – the server sent a random password back. This broker is based on Hexago – so I could use the Gateway6 client with it too. Unlike the freenet6 broker, it did not provide me with a brokered address
Firefox did not like ipv6.l.google.com but Internet Explorer v7 had no problems connecting to the site.
The http://www.sixxs.net/tools/ipv6calc/ site provides some quick information about your IPv6 link. It also provides some fun links, like Virgin Radio.
My conclusions (not verified). Use IPV6 to give unique addresses to all PCs even those behind the NAT. There are two ways to do this, Teredo tunneling and native IPv6. Use the Hexago client and server at this point to get IPv6 addresses for existing machines. I’ll have to look into the native Win2008 and Vista support for ipv6. An alternative to Hexago’s client is AICCU at SixXS. I had to upgrade remote desktop to support IPv6, since the XP version doesn’t support it.
In IPv6 classes no longer exist (Class A, B, C…). Infact even in IPv4 they are dead. The replacement is CIDR which allows variable length network prefixes. This link lets you calculate your CIDR.
“A subnet mask is a bitmask that encodes the prefix length in a form similar to an IP address: 32 bits, starting with a number of 1 bits equal to the prefix length, ending with 0 bits, and encoded in four-part dotted-decimal format. A subnet mask encodes the same information as a prefix length, but predates the advent of CIDR.
CIDR uses variable-length subnet masks (VLSM) to allocate IP addresses to subnets according to individual need, rather than some general network-wide rule. Thus the network/host division can occur at any bit boundary in the address. The process can be recursive, with a portion of the address space being further divided into even smaller portions, through the use of masks which cover more bits.”
The Microsoft site has a very good introduction on TCP/IP . If you are deploying in the office, look at this PDF (link)
Unrelated – Teracopy - good tool for copying files http://www.codesector.com/teracopy.php
Friday, December 26, 2008
Preparing Windows EC2 instance for AMI creation
Review your EC2 settings. Start>All Programs>EC2Service Settings
Clean your disks. Start>All Programs>Accessories>System Tools>Disk clean
Clear out the bytes from deleted space. sdelete –c C: and sdelete –c D: (You can get sdelete from the sysinternals site).
Log off the remote desktop.
Using ElasticFox, right click the running instance and select “Bundle into an AMI”. The S3 bucket name should be globally unique. Note the bucket name and image name carefully (you’ll need it for the registration step). Keep checking the Bundle Tasks tab of ElasticFox to see when it finishes the bundling.
After that, use the “AMI and Instances” tab to register your new AMI. The manifest file name is of the pattern “bundle/imagename.manifest”.
Using the Windows Branded Live site.
Microsoft Live has a service (formerly called Custom Domains) that allows you to create a Window’s Live hosted site. Its called the Partner Live program. (https://partners.microsoft.com/partnerprogram/welcome.aspx)
However trying to locate the free service proved difficult. So I went back to the article in CODE magazine (http://www.code-magazine.com/Article.aspx?quickid=0804112) So in short logon to admincenter.live.com to get started!
Now lets try Google’s Apps. Hmm… no way from the search page to even find it. Found the address on one BLOG page. http://www.google.com/a
Both require that you must modify your DNS records.
Friday, December 12, 2008
Installing Moodle on Amazon EC2
To reduce the disk cost, I decided to create a separate hard disk volume that you can attach to any Windows AMI instance. Any changes that you make to the Moodle are saved to this separate volume. So when you shutdown your instance, the changes are persistent. The only disadvantage is an extra step of attaching the hard disk after the machine is running. The advantage is that you spend less. 1GB of EBS = 0.10 cents per month, vs 3GB AMI = 3x0.15 cents =0.45 cents per month. It is also easier to create snapshots of the disk in this manner. Just right click the volume and create a snapshot. The snapshot is stored on S3.
I’ve created one snapshot of the initial disk – which can be used for new Moodle installs.
Starting up Moodle.
- Start any Windows image (I’ve tried it with ami-ec698d85 Server2003r2-i386-WinAuth-v1.02 and ami-e5698d8c Server2003r2-i386-Win-v1.02) Keep in mind that the Auth server is double the money compared to the vanilla windows.
IMPORTANT: After you right click to launch an instance; In the dialog box, set the Availability zone =”us-east-1c” for the machine. Your volume is located in that zone. Data transfer is free if machine and volume are in the same zone. - Right click the instance and “Show console output”. Wait till you see a message “Message: Windows is Ready to use”. This usually takes about 10 minutes from when you start.
- Once the instance is running, in ElasticFox go to tab “Volumes and Snapshots”. Right click and attach volume (vol-4b9d7922) as “xvdg”.
The disk is automatically mapped to “E” if you do this after the ready message in the “Show console output”. (The volume initially contains an unzipped version of the Windows package installer from moodle.org.)- If you do it before “Windows is ready to use”; you must manually change the drive letters.
(Start>Administrative tools>Computer Management) - Click Storage>Disk Management
- If you do it before “Windows is ready to use”; you must manually change the drive letters.
- Right click the instance and “Get Administrator password”.
- [optional] If you are going to use an Elastic IP, do that now.
- [optional] Modify DNS on your domain nameserver to point to this new instance.
- Right click the instance and “Connect to Public DNS name”.
- Tip (optional) – when you use your browser, you are in Internet Explorer Enhanced Security mode. To turn off Internet Explorer Enhanced Security:
- http://www.windowsreference.com/windows-2003/how-to-disable-internet-explorer-enhanced-security-configuration-ie-esc-in-windows-server-20082003/
- Open “E” drive
- Edit the files E:\server\moodle\config.php (this is not needed when you haven’t configured Moodle for the first time. The file is created during Moodle configuration.)
- Click Start>Run and enter “net stop w3svc”. This stops the IIS server.
- Click “Start moodle.exe”
It should start up. If there is a question about reconfiguration, press 1 and enter to proceed.
The program will continue running in a DOS box with the message “Run STOP Moodle…..” or a blank DOS box. - Click “My public IP” to get the IP address of your instance. (If you haven’t turned off Internet Enhanced Security, you will see a number of warning dialog boxes which you can ignore.)
- From your own PC, use a browser to open that instance. You should see the Moodle page.
Once you are done, you can close the Remote Desktop window (do not logout, just close the window).
Stopping.
Right click the instance and “Connect to Public DNS name”.
Click “Stop Moodle.exe”.
Shutdown the server.
After the server is terminated, delete any Elastic IP addresses that you had attached.
Appendix: Editing Moodle’s config for EC2.
Once you have finished installation, the setup of moodle hard binds the name of the server in the setup files. You must change this if you want to access Moodle from outside the AMI.
Pre-startup - There are two files that should be modified.
1. D:\server\moodle\config.php
Change the line
$CFG->wwwroot = 'http://nooradel';
to
$CFG->wwwroot = 'http://<new public DNS name or elastic IP>';
2. [Optional] D:\server\apache\conf\httpd.conf
Change the line
Servername = localhost:80
to
Servername = <new public DNS name or elastic IP>:80
Helpful links
Setup instructions for Moodle on Windows
http://docs.moodle.org/en/Complete_install_packages_for_Windows
Command line for Amazon EC2.
http://docs.amazonwebservices.com/AWSEC2/2008-12-01/DeveloperGuide/
If you want to find out your own IP address inside a AMI (http://169.254.169.254/latest/meta-data/public_ipv4)
For more details see http://docs.amazonwebservices.com/AWSEC2/2008-05-05/DeveloperGuide/index.html?AESDG-chapter-instancedata.html
Setup the environment to run EC2 command line control tools. (See section on Configuring your workstation).
http://developer.amazonwebservices.com/connect/entry.jspa?externalID=1827&categoryID=100
Key solutions
The key “amazon_ec2.pem” must be used instead of “amazon_ec2.ppk” to retrieve the Windows Administrator password.
Setup in Tools:
- SSH Key template: ${home}\ec2-keys\${keyname}.ppk
- EC2 Private key template: ${home}\ec2-keys\${keyname}.pem
You can re-download the public key by going to the web page. However the private key is not stored on the server. Keep it carefully.
- Amazon_ec2.ppk (putty version of key pair amazon_ec2. )
- Amazon_ec2.pem (EC2 version of key pair amazon_ec2.)
- PK-0…..pem (Amazon account private key)
- CERT-0…pem (Amazon account public key)
Thursday, December 04, 2008
Microsoft Windows Azure and Geneva and Bulldog
Over the last couple of weeks, I’ve seen a lot of information about various products from Microsoft.
Azure
A distributed operating system for the “cloud”. The idea here is that you write to the Azure API on your desktop. Run / debug it on the desktop. When you deploy it to Azure, Microsoft will run this on “server” fabric. You don’t have to worry about individual servers, scalability etc. Since your code could end up running on different servers due to load balancing, all state information must be stored centrally. Azure provides a distributed storage and a distributed SQL Server data storage to address these requirements. Azure is in CTP. You can download the SDK and play around on your own PC. If you want to deploy to Azure, you’ll need a invitation token (these were given out in PDC 2008). For the development machine, you need Windows 2008 or Vista, Visual Studio 2008.
MDM BullDog
Microsoft acquired Stratature’s MDM product (eDM). This is a robust MDM tool that is in its 4th generation. Profisee is the firm spun off by ex-Stratature employees. Ian from Profisee gave an excellent introduction to this tool. What I liked was its out of box Web UI, Workflow, Business Rules and a solid BI focus.
Geneva
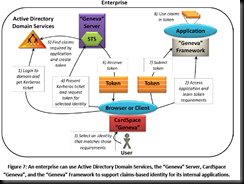
This gets exciting. In the Identity space, there is a shift from applications managing your identity (uid/pwd) to claim based authentication/authorization. To use an application (RP-relying party), you need to provide a token with the appropriate claims from a trusted STS. The IP (Identity provider) STS (Secure Token Service) issues you a token with the claims, after you logon to the STS. It signs the token with a private key. The RP can decode the token and extract the claims to decide whether the user is allowed to use the application. So why is it exciting?
The IP can be Yahoo OpenID, Google, Microsoft Live or even a self issued IP. Your app can choose to trust all these STS’s; or a better way is to trust a single STS and ask the user to get a token from this STS using the token from the first STS. This provides a transparent way to federate identity. Everything is service based that makes it easy for active / passive logon. Geneva provides 3 components – Geneva server which is a Windows based STS, Geneva Cardspace which is an identity selector and Geneva framework which is an API for applications that need to use Geneva. The nice thing is that these are not bound and are based on open standards (WS-Trust, SAML, WS-Security). While searching for this, found that WCF provides a wsFederation binding that can handle claim based authentication in WCF.
Cardspace Identity selector
Enterprise case
Internet case
Using external STS
Multiple STS
Thursday, May 31, 2007
Another growing trend - Virtual PCs
So why virtual?
For one, its easier than keeping a physical machine around. The "overhead" of running in a virtual machine is not too much - about 10-20%. So if you convert an old PC running on a 1GHZ CPU, you can speed it up by running it inside a virtual machine.
The other reason is legacy stuff. I mean all the apps that you accumulated on your last laptop. Moving to your new laptop, you really don't want to repeat all the setup stuff and tweaks you did earlier. Also most of these will probably never get used, and yet you don't want to delete them. So why not convert it to a virtual machine instead?
Disk space is cheap, so you can convert it and forget it, right? Even then, you may want to save some disk space. One nice feature in the VMware Workstation 6 version (not free) is its snapshot and linked clones. Linked clones share the same resources.
Say you start with a plain vanilla XP install (VM_XP).
Next I create a linked clone and install Firefox on it (VM_Firefox).
Then I create another linked clone and install Opera on it (VM_Opera).
The linked clone feature lets all three VMs share the same Windows files - without corrupting each other. So each will have its own linked disk to the original disk. In short this saves you a couple of gigabytes in redundant XP files.
The snapshot feature lets you take a offline snapshot of the PC and its hard disks. Useful when you are about to apply a hotpack and may want to go back :-).
Update: Fast forward to 2014:
The technology that started here, caused Amazon in 2008 to start creating massive server farms of virtual machines. It was the start of the "cloud computing" era.
The next wave - is it Workflow?
The collaboration recognizes that the process requires multiple people to provide inputs / approvals / notifications. So rather than using email, why not build it into the application?
This is where workflow across systems steps in. I've studied SAP's Guided Procedures and their CAF framework. Later this week, when looking at the Microsoft Workflow services, I was struck by how similar the two were!
Next step will be to try out a few scenarios with both technologies
1. Microsoft Workflow Foundation services - possible embedded in Microsoft Sharepoint.
2. SAP Guided Procedures in the SAP Portal.
Wednesday, March 09, 2005
Windows NT/XP security
It is dangerous to allow a person to boot your PC with his floppy disk. This link discusses how you can get administrative access to a Windows XP machine by booting from a floppy disk.
The approach is rather ingenious. It edits the NT SAM database using an offline registry editor.
http://www.cgsecurity.org/nt.html. The utility chgntpw is excellent as an offline registry editing tool. A while back I was trying to find such a utility (see the BLOG on reinstalling Windows), but gave up. This seems promising...
This website also has approaches for admin access to Linux. A link from one of these pages discusses how to change Administrative passwords on Domain controllers - useful for administrators who install NT/XP half asleep ;-)
http://home.eunet.no/~pnordahl/ntpasswd/editor.html
RockXP3
While we are on security, be careful about RockXP3. One of its features is displaying passwords stored in Internet Explorer, Outlook Express and RAS. So if you save such passwords , they can be viewed with RockXP3.